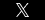Obviously, emails are hearsay evidence that are admissible at trial. Donati v. State is a criminal case that teaches us a lesson in how to get an email into evidence at trial.
Emails are admissible in court. You just have to know what the law requires to admit emails into evidence. In medical malpractice and product liability cases, this is something you often need to do. This case shows us how to present an email at trial and get it into evidence.
The Facts of Donati v. State
If I will have to read a criminal case, I want some whacked-out facts to keep me interested. This case delivers. And this example helps explain how to get emails authenticated and in evidence.
The defendant developed a grudge against a particular bar and bar owner after he was forcibly removed from the premises. Over the course of the next few months, he exchanged various threatening emails with the bar owner and his staff from a variety of different email addresses. 
The defendant, not content to stop there, also began sending emails to the Montgomery County Police Department alerting them to “narcotics activity” at the bar. It is worth mentioning, I guess, that the police found no evidence of this alleged narcotics activity but who knows how hard they looked. The emails to the police department were also sent from several email addresses. [Memo to self: create phony email addresses to send hate mail to anyone who posts a nasty comment on this blog.]
As the tips continued to prove fruitless, the emails became increasingly bizarre The police became suspicious and made the connection that these emails were likely being written by the same person. Following up on these and other marijuana-related suspicions – which I have no idea how they got – the police arrested the defendant. At his home, police found dozens of email addresses written on sheets of paper, many of which matched the email addresses used to communicate false information to the police and threats to the bar owner. That’s hard evidence to run from, right?
He was convicted of marijuana-related offenses and fifteen counts of email harassment and the providing of false statements. He appealed his conviction based on, among other things, the trial court’s failure to authenticate the emails he sent back and forth with the police. In denying his appeal, the Maryland Court of Special Appeals dealt for the first time with the proper means of authenticating an email document for admission in court.
Email Authentication Issue
The prosecution’s problem was a genuine one. How do you get the emails authenticated? Defendant claimed that the prosecution did not do what it had to do to allow the jury to consider, and convict in this case, the emails.
There are many paths to authenticate e-mails. It can be as easy as getting the witness who received the email to testify that the printed email was received. Emails also usually show the source so authentication can be done just like U.S. Mail can be authenticated. There is also the business record exception. So, on its face, this is not a big deal.
But the problem is emails are so easy to fake, right? Unlike medical records, email authentication is a real thing because it can be tampered with so easily. The Maryland Court of Appeals has underscored this concern, warning that trial judges should be especially wary of admitting evidence of modern means of communication and social media, which may be readily fabricated. Some think our courts have set the bar a little too high.
Are Emails Admissible in Court?
Emails are admissible in court. The key is laying the foundation to admit the emails into evidence at trial.
So emails can be admissible in a trial as evidence, subject to certain requirements and procedures. In general, emails may be introduced as evidence if they are relevant to the case and meet the standards of authentication and hearsay.
To authenticate an email, a party seeking to admit it must be able to show that the email is what it purports to be, and that it was sent or received by the person claimed to have sent or received it. This can be established through various means, such as testimony from the sender or recipient, or technical evidence showing the email’s metadata.
Maryland Rule
Maryland Rule 5-901(a) outlines the general rule concerning authentication. “The requirement of authentication or identification as a condition precedent to admissibility is satisfied by evidence sufficient to support a finding that the matter in question is what its proponent claims.” Ultimately, authentication serves the purpose of “requiring the presentation of evidence sufficient to show that the evidence sought to be admitted is genuine.”
Hearsay Problem
In addition, emails may be subject to the hearsay rule, which generally prohibits the admission of out-of-court statements made by someone other than the witness who is testifying, unless an exception to the rule applies. One such exception is the business records exception, which allows for the admission of documents created and kept in the ordinary course of business, including emails.
Catch-All Exception
Even if an email is relevant, authentic, and admissible under an exception to the hearsay rule, the court may still exclude it if the email is deemed to be unfairly prejudicial or confusing, or if its probative value is substantially outweighed by the danger of unfair prejudice, confusion, or waste of time.
The Court’s Ruling on Email Authentication and Admissibility
The court underscored that emails are admissible in court but the question was whether the proper authentication and admission procedures were used in this case. In addressing this issue, the court cited cases dealing with the proper procedure for the authentication of text messages. The court admitted a lack of precedent for authenticating email communications. But it really is the same idea.
The court started from the premise that the list of methods in Maryland Rule 9-501(b), which controls the authentication of documents, is not exhaustive, and therefore methods not listed may be appropriate for use in authenticating email. The court cited Lorraine v. Markel Am. Ins. Co., a Maryland federal case, for the proposition that e-mail messages may be authenticated by either (1) direct evidence or (2) circumstantial evidence.
How to Present Email Evidence in Court
Email Authentication By Direct Evidence
An e-mail could be authenticated by direct evidence alone if its author or proponent testifies to producing the contents of the email. An e-mail may also be authenticated by direct evidence when someone with personal knowledge of the email, such as someone who helped write or edit it, attests to its authenticity. Authentication by direct evidence is conclusive in itself, but sometimes it is only possible to establish the authenticity of one side of the communication.
With Mr. Donati, the police officers were each able to attest to the authenticity of their own responses to Mr. Donati’s e-mails, but nobody could directly attest to the authenticity of the e-mails allegedly written by Mr. Donati, especially since Mr. Donati denied he was their author. That’s the problem here, right? The authenticity of Mr. Donati’s side of the communication, which was essential to upholding his conviction for e-mail harassment, could only be established through circumstantial evidence.
Email Authentication By Circumstantial Evidence
 When direct evidence is unavailable to establish the authenticity of an email, circumstantial evidence may be used. Examples of circumstantial evidence that may be used by the court in authenticating emails include the sender’s IP address, the contents of the e-mail (i.e. do they contain information that only the alleged sender would possess?), the use of names or nicknames, and any other identifying factors that could link an e-mail address to a certain person as to its sender or author.
When direct evidence is unavailable to establish the authenticity of an email, circumstantial evidence may be used. Examples of circumstantial evidence that may be used by the court in authenticating emails include the sender’s IP address, the contents of the e-mail (i.e. do they contain information that only the alleged sender would possess?), the use of names or nicknames, and any other identifying factors that could link an e-mail address to a certain person as to its sender or author.
The piece of circumstantial evidence that doomed Defendant and authenticated the e-mails as being written by him was the paper found in his house with the various email addresses recorded on it, some of which were used to communicate lies to the police and threats to the bar owner.
When coupled with the fact that the e-mails all covered the same subject, were written in the same tone, written during the same time period, and that Mr. Donati often followed up his e-mails with phone calls, all circumstantially authenticated the e-mails in the eyes of the court as being authored by Mr. Donati.
Combined with the direct evidence provided by the police officers as to the authenticity of their half of the electronic communications, the court found sufficient grounds to uphold the authentication of the e-mails by the trial court.
How to Present Email Evidence in Court Though a Witness
Here is an example of a lawyer admitting an email through a witness by laying a proper foundation:
Lawyer: Ms. Doe, I would like to direct your attention to an email sent from John Doe to you on March 3, 2023 that has been remarked as Exhibit X. Do you recall receiving this email?
Witness: Yes, I do.
Lawyer: And can you confirm that this email is a true and accurate copy of the email you received on that date?
Witness: Yes, it is the email I received.
Lawyer: Thank you, Ms. Doe. Now, looking at the email, can you confirm that it was sent from John Doe’s email address and that it contains the same content as the email you received on March 3, 2023?
Witness: Yes, that is correct.
Lawyer: Your Honor, at this time, I would like to move to admit Exhibit X into evidence.
Other Email Evidentiary Issues of Note
I could not work these into the post, but here are more nuggets from this case.
- Prior to the 2012 amendment to Maryland Rule 3-805 (the e-mail harassment statute), each e-mail sent was the unit of prosecution used in charging the defendant. Since that amendment, each course of conduct (or series of related emails) is now the unit of prosecution under Rule 3-805. Criminal lawyers understand what I’m saying here but I really don’t.
- The Federal Rule of Evidence 901 provides the standard for the authentication of evidence, including emails. Rule 901(a) requires that the proponent of the evidence must present sufficient evidence to support a finding that the item is what the proponent claims it is.
- The court reiterated the 5 step approach set forth by the U.S. Supreme Court in Neil v. Biggers 409 U.S. 188, 189 (1972) for determining the reliability of in-court voice identification: (1) the ability of the witness to hear the assailant speak, (2) the witness’s degree of attention, (3) the accuracy of any prior identifications the witness made, (4) the period of time between the incident and the identification, and (5) how certain the witness was in making the identification.
- The court also reiterated the wide latitude that counsel has in performing closing arguments, while still emphasizing the fact that counsel is not permitted to comment upon facts, not in the evidence or invite the jury to do so.
One other point I think is critical. If you are trying to admit emails in a civil case and you are worried it might be an issue, send requests for admission for authentication. If you wait until trial and there are complications, you are just asking for trouble.
 Maryland Injury Law Center
Maryland Injury Law Center